02.03
Summary
Aardvark contained several reflected, DOM based XSS vulnerabilities. Due to CSRF protections, exploiting these vulnerabilities remotely was non-trivial.
How did it work?
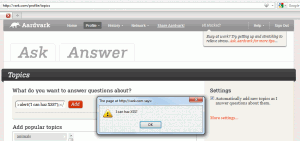
1. “Topics” profile page
When adding a new topic to your profie via the Topics page, the text of the new topic was parsed as HTML, which caused any JavaScript contained in the text to be executed.
I tracked down the relevant function (add_interest_to_interface) in
the JavaScript and ran it through a pretty-printer. Here’s what it
looked like:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 | var add_interest_to_interface = function (user_term) {
user_term = $.trim(user_term);
if (user_term.match(/any (.*) question/)) {
user_term = user_term.replace(/any (.*) question/, "$1");
}
if (interest_is_active(user_term)) {
return false;
};
user_interests[user_interests.length] = user_term.toLowerCase();
tmpl = '<li class="interest" style="display:none">' +
'<form class="delete_interest" title="Remove this topic" method="post" action="/interests/destroy_by_user_term">' +
'<input type="image" src="/images/blank.png"/>' +
'<input type="hidden" value="#{escaped_user_term}" name="user_term"/>' +
'</form>' +
'<span class="user_term">' +
'#{user_term}' +
'</span>' +
'</li>'
$('#user_interests').append($.tmpl(tmpl, {
'user_term': user_term,
'escaped_user_term': $.escapeHTML(user_term)
}, {
escape: false
}));
$('#user_interests li:last').fadeIn();
$('.topic-menu').each(function () {
add_styles($(this));
});
return true;
};
|
The code was generating a fragment of HTML to be used as a template
(look at the variable tmpl). The vulnerability was caused by the use of
a non-escaped version of the user’s input within the template
(#{user_term} versus #{escaped_user_term}). The fix was simple:
always use the escaped version.
When the page was refreshed, the new topic was loaded from the database, causing it to be sanitized properly.
2. “Questions you’ve asked” page
This vulnerability functioned in almost exactly the same way as the one above. It occurred on the Questions you’ve asked page when updating the topic for an existing question (“Question about…”). There were two separate locations on the page where the un-sanitized user input was used.
More Information
The vulnerability mentioned here has been confirmed patched by the Google Security Team. I owe them a ton of thanks for organizing this program and giving me a chance to improve my skills.
Interested readers are encouraged to take a look at other vulnerabilities I’ve reported under Google’s Vulnerability Reward Program.

Comments