02.01
Summary
Google Code contained a static HTML page that was vulnerable to a reflected, DOM-based XSS vulnerability.
How Did It Work?
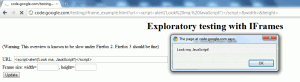
The page in question is located at
http://code.google.com/testing/iframe_example.html. I originally
came across it when I was performing a Google search for an unrelated
vulnerability: I’m not sure how I would have found it otherwise. ![]()
The page itself is fairly straightforward. It uses JavaScript to parse the query string and extract key/value pairs; it then document.write to add the data provided by the user directly to the page. If you look at the HTML on the page right now, you can see that user input is sanitized using JavaScript’s escape function: in the past, that was not the case. That lack of sanitization is what allowed the vulnerability to occur.
More Information
The vulnerability mentioned here has been confirmed patched by the
Google Security Team. I owe them a ton of thanks for organizing this
program and giving me a chance to improve my skills (and for putting up
with me even when I report vulnerabilities that, unlike this one, affect
only IE 6 / 7 ![]() )
)
Interested readers are encouraged to take a look at other vulnerabilities I’ve reported under Google’s Vulnerability Reward Program.