04.05
Summary
Certain sections of the Google Support Forums (hosted on google.com) were vulnerable to a persistent XSS attack. An attacker could submit posts containing JavaScript URIs in specific locations, triggering the execution of arbitrary JavaScript.
How did it work?
A few of Google’s support forums (for instance, Webmaster Central)
allow users to embed external content in their posts. This content
includes links to external websites, search results, YouTube videos,
etc. When the post is actually submitted to the server, the URL to the
content is included in one of the POSTed fields, called wpiprsi (one
example looked like
1%26asdf%26%26%26asdf%26http%253Awww.google.com%26%26%26%26%26%26%26%26%26%26%26%26%26%26%26%26).
By manipulating the URL that was submitted, it was possible to execute JavaScript.
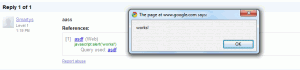
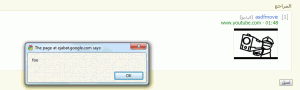
The simplest example involved links to websites. By modifying the URL in
the example above, changing it from http://www.google.com to
javascript:alert('works'), it was possible to create a link that would
execute JavaScript when clicked. Of course, an XSS vulnerability that
requires user interaction like that is less than ideal.
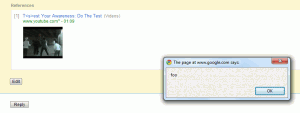
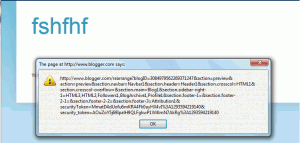
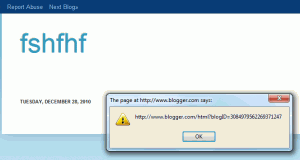
The other, more useful attack I found involved the ability to embed videos. All I needed to do was send a request with the URL for a video swapped out with a JavaScript URI. The malicious URI was put into the src attribute of an embed tag, which allowed it to be executed for anyone who viewed the page.
More Information
The vulnerability mentioned here has been confirmed patched by the Google Security Team. I owe them a ton of thanks for organizing this program and giving me a chance to improve my skills.
Interested readers are encouraged to take a look at other vulnerabilities I’ve reported under Google’s Vulnerability Reward Program.