12.17
Over the past several weeks, I’ve been an active participant in Google’s Web Vulnerability Reward Program. I’ve been writing blog posts about each of the vulnerabilities I’ve reported, publishing them once I’m told that the vulnerability has been patched. I’ve also been keeping up with posts that others have written and submitted to places like /r/netsec, /r/xss, and Hacker News. The posts, in aggregate, have explored many areas of web application security: XSS attacks of varying design, CSRF vulnerabilities, HTTP response splitting, clickjacking, etc. However, the program has attracted quite a large number of participants; I’m sure that I’ve seen only a small fraction of what people have posted.
Thus, the idea for this post came into being. My intention is to find and link to reports that people have written about vulnerabilities found as a part of this program. I’ve done a bit of searching and compiled a few links to start with (I’ve ordered them by the date they were posted). If anyone has suggestions for links to add, post in the comments and let me know: I’ll update the post with them.
| Title | Summary / Notes | Posted |
|---|---|---|
|
Google Calendar CSRF https://nealpoole.com/blog/ |
Google Calendar was vulnerable to a series of CSRF vulnerabilities. In at least two separate instances, existing countermeasures (CSRF tokens) were not being validated by the application. | 2010-11-30 |
|
Google.com XSS – HTML Code Injection http://tinkode27.baywords.com/ |
Google Maps contained an XSS vulnerability in its “Change default location” feature. The “HTML Code Injection” vulnerability referenced is not a bug: Google Translate has its content properly sandboxed (as the post indicates), mitigating the effects of any vulnerability. | 2010-12-01 |
|
Google Scholar CSRF https://nealpoole.com/blog/ |
Google Scholar was vulnerable to minor but potentially annoying CSRF vulnerabilities in two different pages. The regular search equivalents of both of these pages used CSRF tokens to mitigate these problems. | 2010-12-07 |
|
Google.com XSS / Google Spreadsheets Clickjacking http://securitylab.ru/ [English] |
Google.com was vulnerable to an XSS attack (the exact details are unclear). It also appears that it was possible to perform a clickjacking attack using a Google Spreadsheet. | 2010-12-08 |
|
Google XSS Flaw in Website Optimizer Scripts explained http://www.acunetix.com/blog/web-security-zone/ |
Google’s Website Optimizer produced “control scripts” that caused websites to become vulnerable to XSS attacks. The attack required that the site already be vulnerable to a cookie injection vulnerability (discussed in more detail in the comments). | 2010-12-09 |
|
Finding security issues in a website (or: How to get paid by Google) http://adblockplus.org/blog/ |
Four different vulnerabilities: one basic XSS in YouTube Help, one XSS in onclick attributes, one HTTP Response Splitting vulnerability, and one last XSS in a tooltips script for Website Optimizer. | 2010-12-11 |
|
Gmail+Google Chrome XSS Vulnerability http://spareclockcycles.org/ |
Gmail contained an XSS vulnerability in the way it handled attachment names in Google Chrome. | 2010-12-14 |
|
XSS in YouTube http://www.ebanyu.com.ar/ [English] |
YouTube’s inbox allowed an attacker to turn a JSON response into an XSS vector. The attacker needed to know the target’s session token in order to exploit the vulnerability. | 2010-12-14 |
|
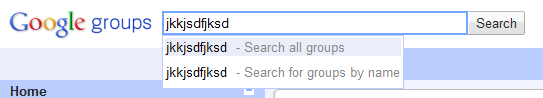
New Google Groups, Non-Persistent XSS https://nealpoole.com/blog/ |
The new Google Groups interface contained an XSS vulnerability in its search functionality. The vulnerability required some user interaction to be activated. | 2010-12-17 |
|
DoubleClick HTTP Header Injection / XSS http://www.cloudscan.me/ |
The Doubleclick Ad CDN was vulnerable to HTTP Header Injection and cross site scripting attacks. | 2010-12-21 |
|
XSS in Google Support Contact Form https://nealpoole.com/blog/ |
One page in Google’s Help Center was vulnerable to a reflected cross-site scripting attack. | 2010-12-21 |
|
Security Token Prediction in Google Scholar Alerts http://www.garage4hackers.com/ |
Google Scholar’s Alerts feature used predictable security tokens in its URLs. This weakness allowed an attacker to create / list / delete alerts on behalf of other users. | 2011-01-05 |
|
XSS in Google Shopping, Maps and Blogs http://apoup.blogspot.com/ |
Google Shopping, Google Maps, and Google Blog Search were vulnerable to an unspecified cross-site scripting attack. There are more details available on the reporter’s blog (in the original Japanese and in English). | 2011-01-27 |
|
XSS Vulnerability in Google Code Static HTML https://nealpoole.com/blog/ |
Google Code contained a static HTML page that was vulnerable to a reflected, DOM-based XSS vulnerability. | 2011-02-01 |
|
XSS in Google Analytics via Event Tracking API http://spareclockcycles.org/ |
Google Analytics was vulnerable to a persistent XSS attack. A malicious attacker could generate fake events containing malicious HTML that would be executed on the Analytics dashboard. | 2011-02-03 |
|
Non-Persistent XSS in Aardvark https://nealpoole.com/blog/ |
Aardvark contained several reflected, DOM based XSS vulnerabilities. Due to CSRF protections, exploiting these vulnerabilities remotely was non-trivial. | 2011-02-03 |
|
Persistent XSS in Google Baraza / Ejabat https://nealpoole.com/blog/ |
Google Baraza (www.google.com/baraza/) and Google Ejabat (ejabat.google.com) were vulnerable to a persistent XSS attack. A malicious user could create a post that would trigger JavaScript when an image or link was clicked on. | 2011-02-03 |
|
Persistent XSS in Blogger Design Preview https://nealpoole.com/blog/ |
Blogger’s Design Preview functionality served up author-generated content in the context of blogger.com, allowing an author to perform an XSS attack against a blog administrator. | 2011-02-03 |
|
Multiple Vulnerabilities in Google Applications http://d.hatena.ne.jp/masatokinugawa/ [English] |
The post covers three different types of vulnerabilities that the author came across. | 2011-02-07 |
|
Persistent XSS in Google Finance http://benhayak.blogspot.com/ |
Google Finance did not properly escape the names of user-created portfolios when using them in JavaScript. As a result, it was possible to craft a name that would cause XSS. | 2011-02-16 |
|
Persistent XSS in Google Website Optimizer http://benhayak.blogspot.com/ |
By using javascript: URIs in place of regular URLs when creating an experiment, the author of the post was able to craft a persistent XSS attack. | 2011-02-27 |
|
Reflected MHTML Injection in Google Support (mail.google.com) http://www.wooyun.org/ [English] |
It was possible to inject a valid mhtml document into a support page hosted on mail.google.com. As a result, IE users who browsed to a malicious URL using the mhtml protocol handler could have trigger an XSS attack. | 2011-03-03 |
|
How I Almost Won Pwn2Own via XSS http://jon.oberheide.org/blog/ |
The Android Market was vulnerable to an XSS attack due to a lack of output sanitization. Due to how the Android platform works, the vulnerability could have been used to download and execute arbitrary code onto phones. | 2011-03-07 |
|
Gaining Administrative Privileges on any Blogger.com Account http://www.nirgoldshlager.com/ |
Blogger was vulnerable to an HTTP Parameter Pollution vulnerability. By providing the blogID twice in the request (once with a blogID controlled by the attacker and once with a blogID controlled by the victim) it was possible to make requests on behalf of a blog where you were not authorized. | 2011-03-10 |
|
Reflected XSS in mail.google.com http://www.cloudscan.me/ |
Gmail did not properly sanitize input provided by the user in the URL and the cookie. As a result, it was vulnerable to several reflected cross-site scripting attacks. | 2011-03-30 |
Let me know what you think in the comments!
Update (12/21/2010): The comments have spoken and I’ve added a new vulnerability to the list.
Update 2 (12/21/2010): Adding another vulnerability that I reported to the list.
Update 3 (1/6/2011): fb1h2s emailed me about a vulnerability he reported. It has been added to the end of the list.
Update 4 (1/27/2011): We have another vulnerability report submitted via the comments.
Update 5 (2/3/2011): Five new reports have been added to the list, all of them XSS vulnerabilities!
Update 6 (3/4/2011): Three new reports have been added to the list.
Update 7 (3/7/2011): Added a cool new report about an XSS vulnerability in the Android marketplace
Update 8 (3/10/2011): Nir Goldshlager has written in with a link to his first report, an authentication bypass / HTTP Parameter Pollution vulnerability in Blogger.
Update 9 (3/30/2011): New Gmail XSS. Super happy fun time.